12. Storing secrets in DFM database
12.1. What is “a secret”?
To connect to various devices, DynFi Manager has to authenticate. For example, in order to establish SSH connection to a device, DynFi Manager has to use a password or a SSH private key. If a user decided to use Automatic Login in Direct View, the password has to be saved. Also, to send e-mails, DynFi Manager needs to authenticate to SMTP server. All these passwords and private keys are called “secrets” below.
12.2. Default storage format
By default secrets in DynFi Manager’s database are kept in unencrypted way.
12.3. How to turn on encryption of secrets in the database?
To turn on encryption of the secrets in the DynFi Manager’s database, it is enough to specify encryptionPassword option in
DynFi Manager’s configuration. For example, it can be added to configuration file (default /etc/dynfi.conf) the following way:
encryptionPassword=my_very_L0ng_and_R4ndom_encryption_P@SSWORD
When DynFi Manager starts next time, it will detect that encryptionPassword has been specified and secrets in the database
are not encrypted, so it will encrypt all secrets during this start-up.
It is advised to create database backup before.
For other ways of tuning the configuration, refer to DFM Configuration chapter.
12.4. How to change encryption password?
Once the encryption password has been set in configuration, it cannot be changed without migrating encrypted secrets from being encrypted using old password to being encrypted using new password. In case you need to change your encryption password (e.g. because it has been compromised), it is possible using DynFi Manager.
To migrate to new encryption password, stop DynFi Manager first. (It is advised to create database backup too.) Then run DynFi Manager’s encryption wizard to change or drop encryption password (you can also specify path to your custom configuration file if not using the default location):
java -jar /path/to/dynfi.jar changeEncryptionPassword [--config /path/to/my/custom_dynfi.conf]
To navigate, use arrows and tab keys, select using [Enter] key. First, the wizard will inform which database is used:
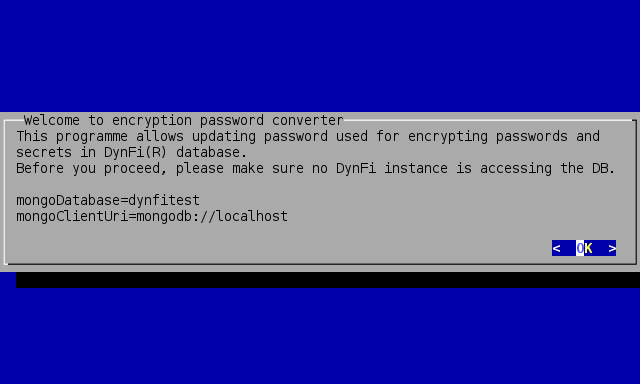
Encryption wizard intro
In case of databases in which secrets are not encrypted, the wizard will only allow entering new password twice:
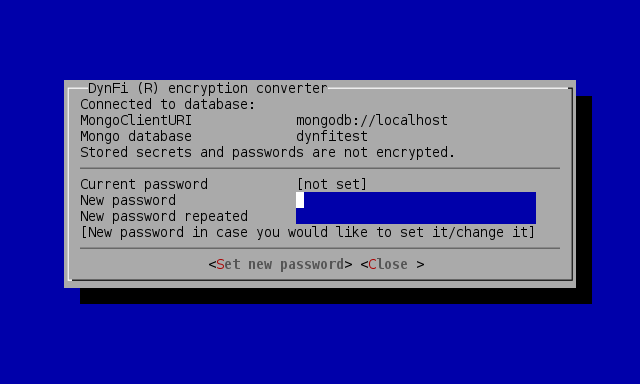
Encryption wizard with not encrypted secrets
In case of databases in which secrets are already encrypted, the wizard will also require the current (old) password:
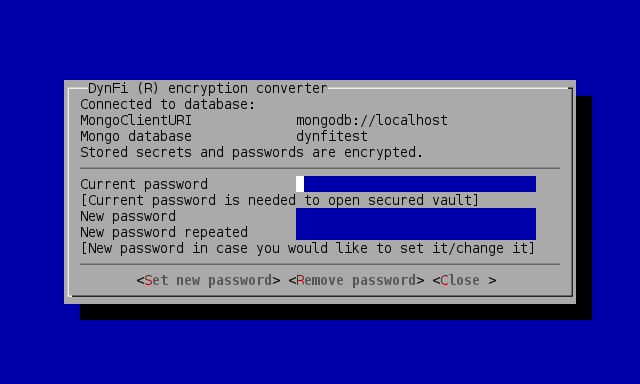
Encryption wizard with encrypted secrets
In order to set or update encryption password, enter the new encryption password twice and select <Set new password>:
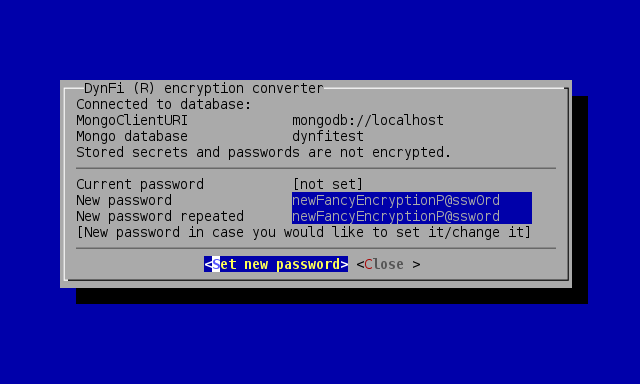
Encryption wizard new password required twice
The conversion will not begin if not confirmed:
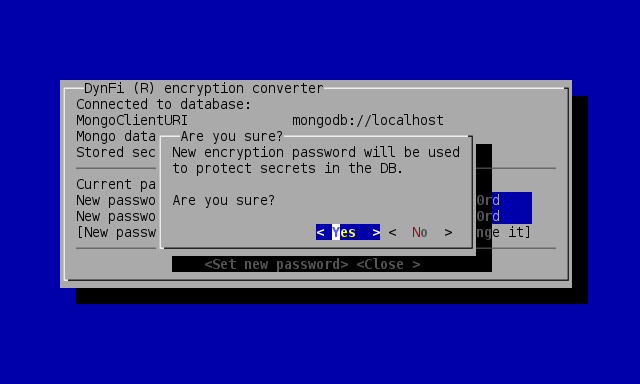
Encryption wizard confirmation before conversion
Next, progress can observed (if there are many secrets and conversion takes a while):
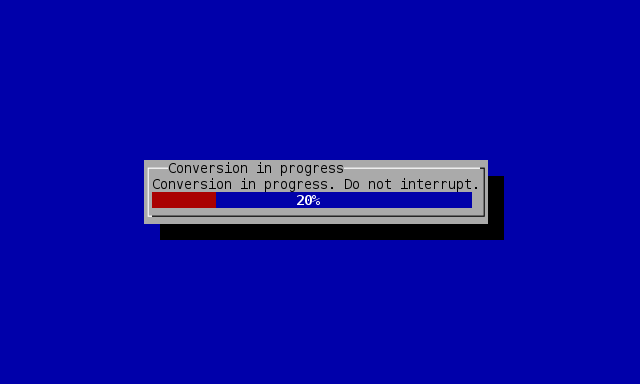
Encryption wizard conversion progress
After completing the conversion, it is confirmed by the wizard.
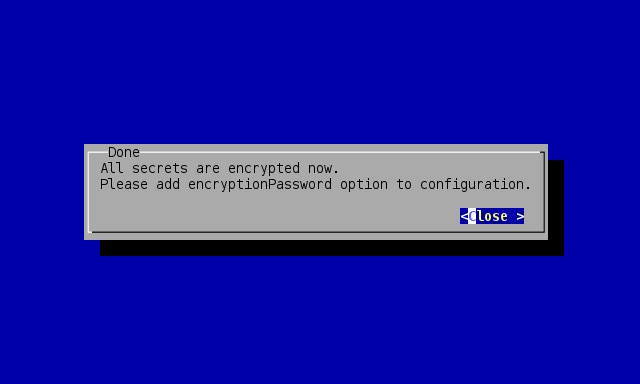
Encryption wizard conversion finished confirmation
Now the new encryptionPassword has to be set in DynFi Manager’s configuration.
If the encryption password should be not used any longer, the wizard allows that too. To do that, just select <Remove password> button and follow very similar procedure. After completion, do not forget to remove encryptionPassword from DynFi Manager’s DFM Configuration.
12.5. Performance check
Before encrypting the secrets (either by the first time by setting encryptionPassword or by running the encryption
wizard by changeEncryptionPassword command) DynFi Manager performs a little benchmark to check if the performance
of encryption is satisfactory for reasonable usage.
In case the poor performance is detected, enabling the the encryptionPassword is abandoned. This can be manually
overridden using the encryption wizard.
12.5.1. How to improve the performance
The performance of encryption depends on many factors, e.g. on hardware, operating system and configuration of Java. To improve gathering entropy needed for encryption and the encryption itself, one can try several things:
using /dev/urandom, by setting
-Djava.security.egd=file:/dev/urandomparameter or modifyingjava.securityfile (please read about /dev/urandom ),generating more entropy, e.g. using
havegedor other means,using CPU with AES-NI enabled,
setting
encryptionCachingEnabled=truein DFM Configuration.
12.6. I have lost my encryption password
In case the encryption password has been lost or forgotten, there is no way to recover that in DynFi Manager. If the secrets in database are encrypted and the encryption password has not been provided or is incorrect, DynFi Manager will not start.
12.7. How are user passwords stored?
User passwords (i.e. the passwords that are used by users to log in) are stored in a different way, using password
hashing algorithm bcrypt. The default cost of bcrypt hashing (“the strength of the hash”) can be overridden in configuration
using bcryptCost option, e.g.
bcryptCost=14
Be aware, that incrementing the bcryptCost by one should double the CPU time needed to hash and verify password.
Also, the cost factor of already stored users’ passwords is not changed until the password is changed. Therefore in order to
increase “hash strength” after increasing bcryptCost, a user has to change the password.
Please note that your password will never be secure (even using the most sophisticated cryptography solutions), if it is easy to guess. Avoid easy passwords, especially if they can be find in dictionaries. Use small and upper caps, digits and special characters to increase the strength of your password. Never use the same password in two or more systems.