21. LDAP Authentication
DynFi Manager integrates with LDAP to allow user authentication and synchronization of user details and roles.
DFM uses LDAP username/password to authenticate user with LDAP. It expects LDAP to provide:
groups user belongs to,
user’s full name,
user’s e-mail.
When LDAP integration is used, it’s not necessary to create user accounts in DFM. DFM does it automatically, by fetching the above data from LDAP after successful authentication.
DFM doesn’t use LDAP to configure the following settings (they can be managed in DFM as usual):
two-factor authentication,
assigning users to device groups,
user’s session timeout.
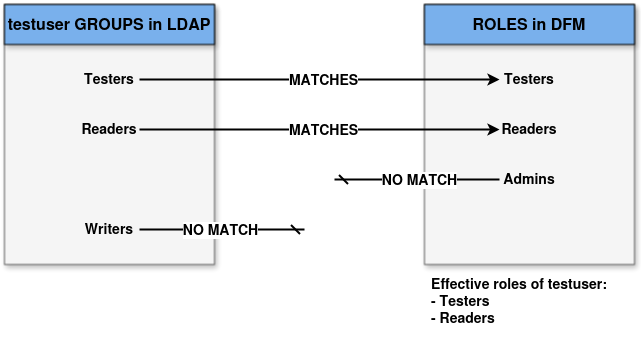
21.1. LDAP groups and DFM roles
LDAP groups are treated as DFM roles. DFM retrieves the user’s LDAP groups at each login and checks if these groups match the roles which exist in DFM. If a group has a corresponding role (both having exactly the same name), the user is granted all the permissions associated with this role.
21.2. Configuration
LDAP integration is not configured by default; it has to be set up using properties listed below. It is recommended to configure it in the dynfi.conf configuration file, but other options are available. See DFM Configuration for details.
All LDAP properties except for ldapUseSSL, ldapDefaultDeviceGroup, ldapGroupSearchAttributeFormat,
ldapSystemUser, ldapSystemPassword are mandatory.
21.2.1. ldapHost
Domain name or IP address of LDAP server, e.g. ldap.mydomain.com.
21.2.2. ldapPort
The port on your LDAP server, e.g. 389 or 636.
21.2.3. ldapUseSSL
Set true to use LDAPS protocol. The default value is false.
21.2.4. ldapUserSearchBaseDn
The base DN where DFM should look for users, e.g. ou=people,dc=dyn,dc=fi.
21.2.5. ldapUserSearchAttribute
The LDAP attribute which corresponds to the user’s username, e.g. uid. It’s used to identify users, along with the
ldapUserSearchBaseDn property.
21.2.6. ldapUserNameAttribute
The LDAP attribute which corresponds to the user’s full name, e.g. cn. It’s displayed as full name in DFM.
21.2.7. ldapUserEmailAttribute
The LDAP attribute which corresponds to the user’s email, e.g. email. It’s used as the user’s email in DFM.
21.2.8. ldapGroupSearchBaseDn
The base DN where DFM should look for groups, e.g. ou=groups,dc=dyn,dc=fi.
21.2.9. ldapGroupSearchAttribute
The LDAP attribute used to determine the user’s membership in the group, e.g. memberUid.
21.2.10. ldapGroupSearchAttributeFormat
The format of the above attribute. By default, only the username is used, but, some LDAP systems may expect the full DN
of the user. Use {0} as a placeholder for the username, e.g.: CN={0},CN=people,CN=appdir,DC=dynfi,DC=com.
21.2.11. ldapGroupNameAttribute
The LDAP attribute which corresponds to the group’s name, e.g. cn.
21.2.12. ldapSystemUser
DN of the user used to search for groups and user details, e.g. uid=reader,ou=people,dc=dyn,dc=fi. Can be omitted if
anonymous access is allowed.
21.2.13. ldapSystemPassword
Password for the above user.
21.2.14. ldapDefaultDeviceGroup
The name of the default DFM device group to be used for LDAP users, e.g. mygroup. If not set user is granted access to
all devices.
21.3. Uniqueness of username and e-mail
Username and e-mail are unique in DFM. If a DFM account with given username and/or e-mail exists, the LDAP user with the same username and/or e-mail won’t be able to log in. Such existing DFM account can be marked as LDAP account which allows LDAP login (see the next section).
Conflicts of username/e-mail on login are logged in both the DFM event log and dynfi.log, see DFM Logs.
21.4. DFM account vs LDAP account
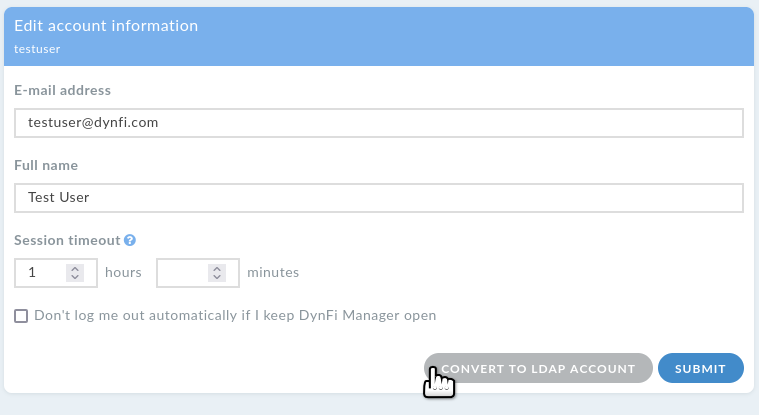
User can either use LDAP credentials or credentials configured in DFM account, they can’t be used interchangeably. The existing DFM account can be converted to LDAP account and vice versa in Edit account information widget (Manage users -> choose the user -> Edit account). Please note that if you mark the account as non-ldap, providing a new user password is mandatory. This operation affects only DFM, nothing is changed in LDAP.
21.5. Modifying user properties
All properties retrieved from LDAP (full name, email, assigned roles) can only be changed in LDAP; it is not possible to override them in DFM. The rest of the properties can be managed in DFM in a usual way.
21.6. Examples of complete configuration
OpenLDAP on the same machine as DFM, SSL enabled, anonymous search allowed, domain: dyn.fi, DFM users in OU=people, DFM groups in OU=groups:
ldapHost=localhost
ldapPort=636
ldapUseSSL=true
ldapUserSearchBaseDn=ou=people,dc=dyn,dc=fi
ldapUserSearchAttribute=uid
ldapUserNameAttribute=displayName
ldapUserEmailAttribute=mail
ldapGroupSearchBaseDn=ou=groups,dc=dyn,dc=fi
ldapGroupSearchAttribute=memberUid
ldapGroupNameAttribute=cn
Active Directory, SSL disabled, domain: dynfi.com, DFM users in OU=people, DFM groups in OU=groups, ldapuser can search for groups and user details:
ldapHost=192.168.122.136
ldapPort=389
ldapUseSSL=false
ldapSystemUser=CN=ldapuser,CN=Users,DC=dynfi,DC=com
ldapSystemPassword=123456
ldapUserSearchBaseDn=OU=people,DC=dynfi,DC=com
ldapUserSearchAttribute=cn
ldapUserNameAttribute=displayName
ldapUserEmailAttribute=mail
ldapGroupSearchBaseDn=OU=groups,DC=dynfi,DC=com
ldapGroupSearchAttribute=member
ldapGroupSearchAttributeFormat=CN={0},OU=people,DC=dynfi,DC=com
ldapGroupNameAttribute=cn
ldapDefaultDeviceGroup=some
Active Directory LDS:
ldapHost=192.168.122.135
ldapPort=389
ldapSystemUser=CN=admin,CN=appdir,DC=dynfi,DC=com
ldapSystemPassword=123456
ldapUserSearchBaseDn=CN=people,CN=appdir,DC=dynfi,DC=com
ldapUserSearchAttribute=CN
ldapUserNameAttribute=name
ldapUserEmailAttribute=mail
ldapGroupSearchBaseDn=CN=Roles,CN=appdir,DC=dynfi,DC=com
ldapGroupSearchAttribute=member
ldapGroupSearchAttributeFormat=CN={0},CN=people,CN=appdir,DC=dynfi,DC=com
ldapGroupNameAttribute=cn
ldapDefaultDeviceGroup=some